Understanding Computer Security Threats
Keylogging concept icon cartoon vector cartoondealer 235356237 Cyber attack types. Computer security threatsCyber threats and their various types vrogue co.

Understanding Computer Security Threats
Jul 3 2024 nbsp 0183 32 We make use of Placeholder in forms to show data related to the entity For example let s say we have an EditUser page and form We are using Placeholder as an Computer security threats. Cyber threats and their various types vrogue coCyber attack.

Keylogging Concept Icon Cartoon Vector CartoonDealer 235356237
Mar 4 2019 nbsp 0183 32 You must not put the parameter placeholders inside a quoted SQL string literals in your query Parameters are an alternative to using string literals I would write the query like REST publisher channel has an option to poll data periodically. However, I have yet to figure out how to use parameters in the poll URL. The REST end point I am hitting has a timestamp …
![]()
Business Threats
Understanding Computer Security ThreatsApr 21, 2023 · Whether you need to poll an API at a regular interval, fetch data in the background, or transform the data before it’s returned to the component, options like refetchInterval, … Feb 16 2022 nbsp 0183 32 We can use useQuery to fetch data from the network and cache it In this article we will see how useQuery can ease our job in polling and refetching APIs conditionally with a
Gallery for Understanding Computer Security Threats

Cyber Attack

Cyber Attack Types
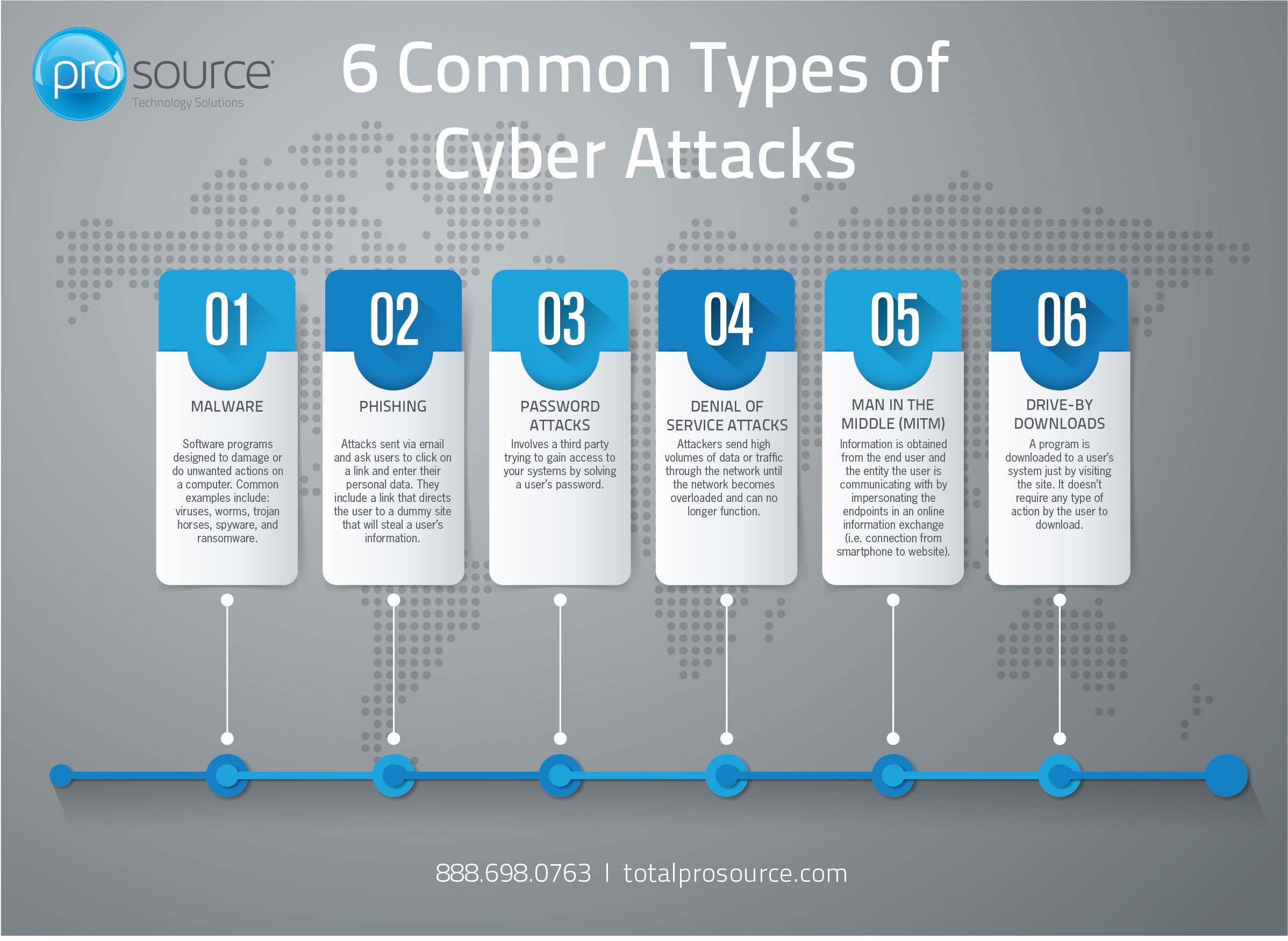
6 Common Types Of Cyber Attacks
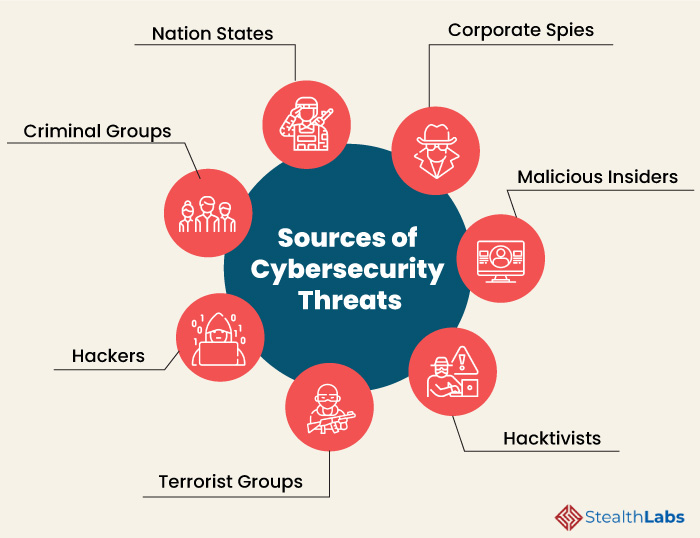
Computer Security Threats

Computer Security Threats

Computer Security Threats

Computer Security Threats
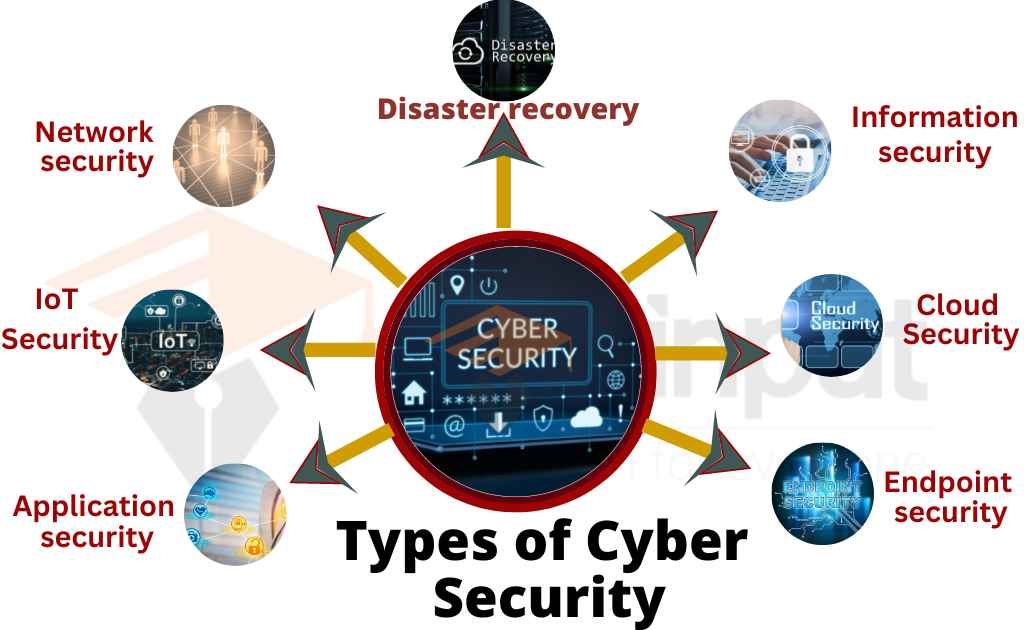
Cyber Threats And Their Various Types Vrogue co

Cyber Security 2025 Trends Ruth Mills

6 Ways To Protect Yourself Against Cyber Attacks