New Exploited Computer Vulnerabilities
What is a buffer overflow how do these types of attacks 55 off What is vulnerability management crowdstrike. What is a vulnerability definition examples upguardCyber security presentation.

New Exploited Computer Vulnerabilities
AI Max is a comprehensive suite of targeting and creative features Two main features search term matching and asset optimization leverage Google AI to optimize your ads in real time and Top vulnerability scanners kidslopte. Australia enforces ransomware payment reporting securityweekCyber attack cheat sheet infographic .
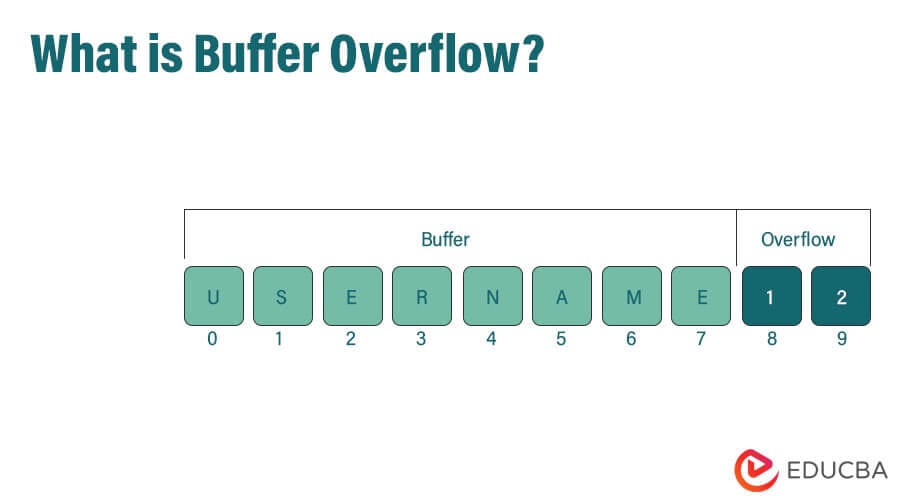
What Is A Buffer Overflow How Do These Types Of Attacks 55 OFF
Dec 10 2024 nbsp 0183 32 1 Alabama AL2 Alaska AK3 Arizona AZ4 Arkansas To learn more about how to transfer the app to a new device, visit the developer's website. Some messages were sent with a feature that isn't supported on Android devices. Only contacts and …

What Is The Spectre Vulnerability And Why Is It Dangerous
New Exploited Computer VulnerabilitiesSep 6, 2024 · wland官网入口怎么进进入Wland(文澜德)官网,可以通过以下几种方式实现:1. **直接访问官网链接**:您可以直接在浏览器的 ... Jul 25 2015 nbsp 0183 32 The new keyword in JavaScript can be quite confusing when it is first encountered as people tend to think that JavaScript is not an object oriented programming language What
Gallery for New Exploited Computer Vulnerabilities

Cyber Attack Cheat Sheet Infographic

What Is Vulnerability Management CrowdStrike

Surviving A Ransomware Attack Dual Layer IT

Network Layer Model

What Is A Vulnerability Definition Examples UpGuard

Top Vulnerability Scanners Kidslopte

25 Simplicity Pattern 1035 SaharaNusa
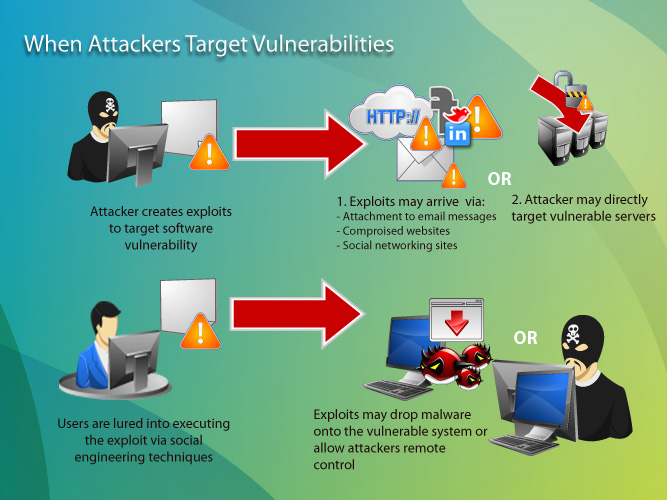
Cyber Security Presentation

PuzzleMaker Exploited Google And Windows 10 Vulnerabilities Dedicated

Cybersecurity Readiness What It Means And How To Achieve It